IT Security: Keeping Data Secure on Cloud Servers
Many customers are recognising the flexibility that cloud servers and services offered by many big players in the IT industry bring. Being able to access your data from a variety of devices over a secure connection allows much greater choice in methods of working.
Although we all recognise the padlock in our web browser address bar as being a sign of security, many people are concerned that others may have access to their data and so implement encryption to keep prying eyes away. This article describes the mechanics of encrypting data on a server and where the weaknesses lie.
Technical Details
The following diagram shows the components and data flow needed to ensure data is securely stored on a cloud server:
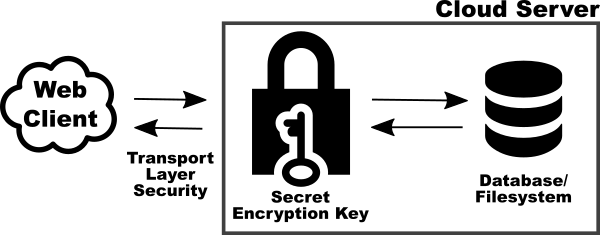
An initial request to read or write cloud data comes from a web browser based somewhere on the Internet. This is secured using Transport Level Security (TLS), which causes the padlock icon to be seen in the browser address bar and ensures the privacy of the data from the browser to the cloud server.
Once the data arrives at the server it must be decrypted by the TLS stack before being passed to its target application. TLS uses a per session key, which is securely negotiated with each browser during the set-up of the communications channel. If the data were not decrypted at the this point it would be impossible to share it with others as its encryption would make it private to a particular browser at a specific point in time. At this stage an unencrypted version of the data is present in memory on the cloud server.
Next the data passes to the encryption provider used by the database, file-system or other destination storage device on the cloud server. To carry out the encryption (and subsequent decryption) of the data a strong key must be known to the process. Commonly this is stored in a configuration file so that server restarts can be performed without further manual intervention. The key itself cannot be encrypted as it needs to be read to provide access to the encrypted data.
For the most secure systems the key is not stored on the server. If the server (or the process encrypting the data) is restarted an operator must manually enter the key to provide access to the encrypted data. Regardless of the procedure used the key will be present in memory on the server whenever the encryption/decryption process is running.
It therefore follows that anyone with access to the memory and/or disk contents of a cloud server also has access to your encrypted data. There is no way around this apart from enforcing physical access control and verifying the integrity of the personnel authorised by it.
Conclusion
Although we often believe a web browser padlock icon is guaranteeing us security, it is actually only verifying that the data securely reaches its destination. Once at its destination physical security alone will protect it, even when all technical measures have been taken.
In the case of cloud or hosting providers we need to examine our contract with the provider, their procedures and most importantly adherence to them. It will be a combination of trust and law that will protect our most sensitive data.